
A Shift in Focus: Why I Redirected My Efforts from OpenGuard to Event-Driven Ansible
Introduction
In today’s rapidly evolving digital landscape, security automation has become a crucial aspect of ensuring the safety and integrity of IT environments. By leveraging automation tools, organizations can effectively monitor security incidents and remediate them promptly, aligning with industry security standards and benchmarks. One such project, OpenGuard, aimed to provide zero-touch security automation by utilizing various open-source tools and software solutions. However, after careful consideration, I made the decision to pause the development of the OpenGuard project. In this blog post, I will explain the reasons behind this choice and shed light on a more suitable alternative.
Understanding OpenGuard and Its Components
OpenGuard was conceived as a comprehensive security automation project designed to protect IT infrastructures and environments. The project consisted of two main components: OpenGuard Engine and OpenGuard Runner. The OpenGuard Engine served as the incident collection and decision-making engine, while the OpenGuard Runner acted as the remediation tool responsible for gathering remediation job details from the OpenGuard app.
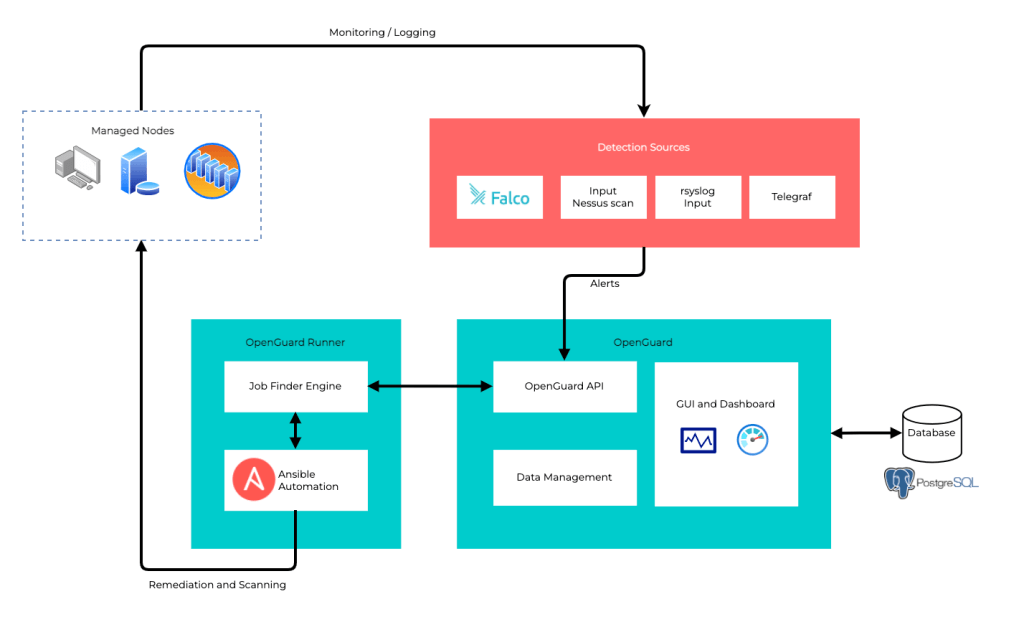
The Need for Multiple Detection Sources
To ensure robust security coverage, OpenGuard planned to integrate multiple detection sources, including Falco, Nessus scan, Prometheus, and more. This approach aimed to provide comprehensive monitoring and alerting capabilities, enabling timely identification of security incidents within the IT environment.
The Role of Ansible in Remediation
For the remediation aspect, OpenGuard utilized Ansible playbooks and Ansible runner. These tools facilitated the execution of automated actions based on predefined instructions. By leveraging Ansible’s powerful automation capabilities, OpenGuard intended to remediate security incidents effectively and efficiently.
The Emergence of Event-Driven Ansible
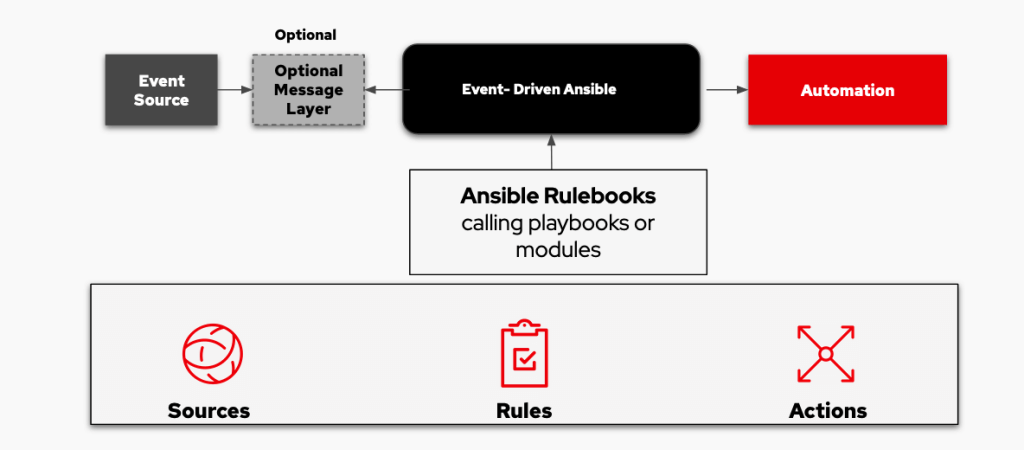
During the course of developing OpenGuard, I became aware of the emergence of Event-Driven Ansible, which introduced a new paradigm for automation. Event-Driven Ansible connects event sources with corresponding actions through rules, allowing for the automation of tasks based on specific events. This approach eliminated the need for developing another separate tool, as it covered the same concept and methodology.
The Benefits of Event-Driven Ansible
As part of the Red Hat Ansible Automation Platform, Event-Driven Ansible provides a powerful event-handling capability that enables the automation of time-consuming tasks and adaptability to change conditions across various IT domains. By leveraging event-driven automation, organizations can achieve enhanced efficiency and responsiveness in their automation workflows.
Contributing to a Fast-Moving Project
Considering the similarities between OpenGuard and Event-Driven Ansible, I decided to shift my focus towards the latter. Contributing to a fast-moving project like Event-Driven Ansible presented an opportunity to align my efforts with a solution that was already well-established and widely adopted. By dedicating my efforts to this project, I could contribute to its further development and maximize my impact within the automation community.
Conclusion
Although the OpenGuard security automation project showed promise, the emergence of Event-Driven Ansible provided a more suitable alternative that eliminated the need for duplicating efforts. By joining the Event-Driven Ansible community, I aim to contribute to the advancement of automation practices and help organizations embrace a more efficient and adaptable approach to their IT operations.
To learn more about OpenGuard and its documentation, please visit: openguard.iamgini.com
NB: It is important to note that during the development of OpenGuard, the project was in its early stages and faced time constraints. As a result, some best practices may not have been fully implemented. This limitation should be taken into consideration when evaluating the project’s capabilities and potential.
Disclaimer:
The views expressed and the content shared in all published articles on this website are solely those of the respective authors, and they do not necessarily reflect the views of the author’s employer or the techbeatly platform. We strive to ensure the accuracy and validity of the content published on our website. However, we cannot guarantee the absolute correctness or completeness of the information provided. It is the responsibility of the readers and users of this website to verify the accuracy and appropriateness of any information or opinions expressed within the articles. If you come across any content that you believe to be incorrect or invalid, please contact us immediately so that we can address the issue promptly.
Tags:
Comments





Leave a Reply