
How to open WinRM ports in the Windows firewall
You might already knew that, Ansible can manage Windows servers as well. And this is a supporting article for Configure Your Windows Host to be Managed by Ansible.
Ansible is using WinRM (Windows Remote Management) to connect to the Windows machines. You need to configure listener and the service on the Windows machine as part of WinRM setup and this is clearly explained in this document.
See other articles to learn how to manage windows using Ansible
- Configure Your Windows Host to be Managed by Ansible
- How to open WinRM ports in the Windows firewall
- Ansible Windows Management using HTTPS and SSL
Ensure WinRM Ports are Open
Next, we need to make sure, ports 5985 and 5986 (HTTPS) are open in firewall (both OS as well as network side).
Open Windows Firewall from Start -> Run -> Type wf.msc.
(Or Open Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security -> Windows Firewall with Advanced Security -> Inbound Rules.)
Right-click the Inbound Rules node and choose New Rule.
Select the predefined rule “Windows Remote Management” from the dropdown option
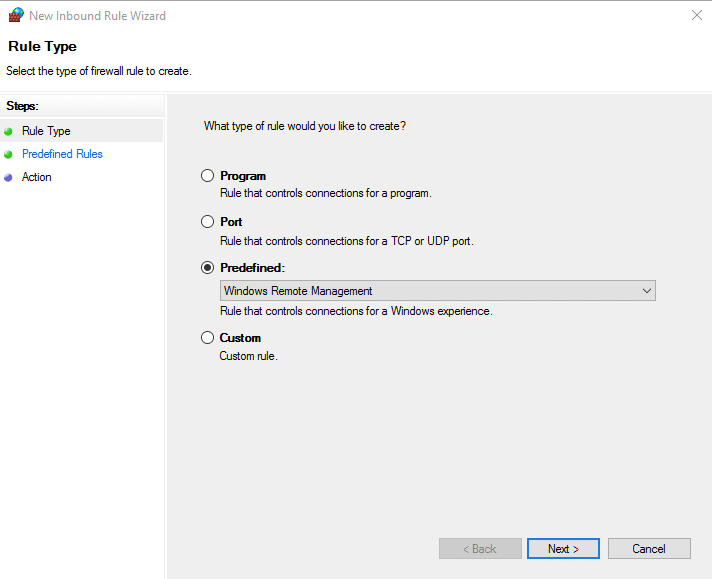
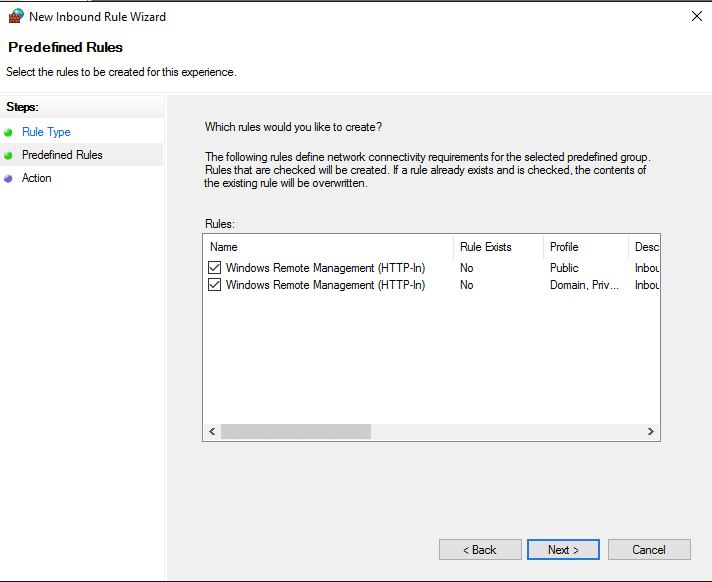
Select Rules as needed
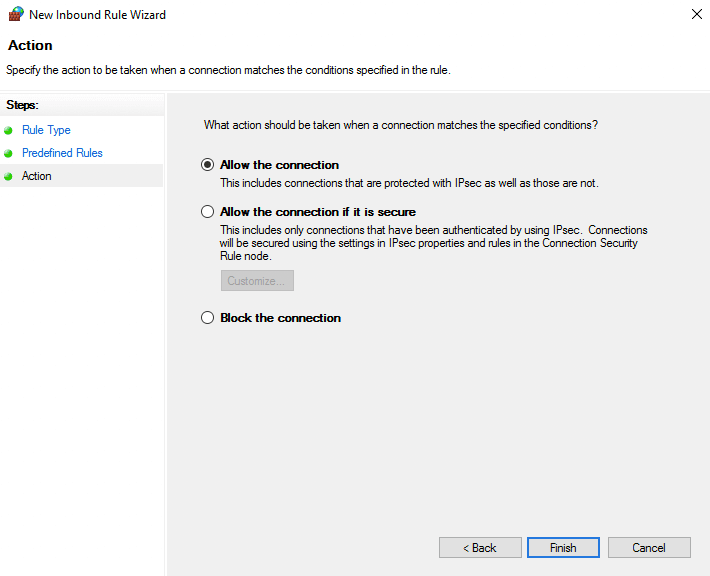
Select Allow the connections
Verify the same in console
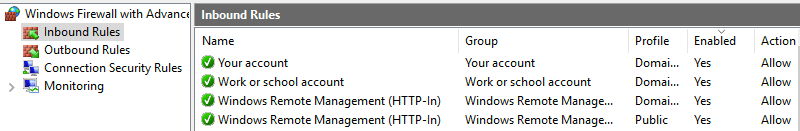
Verify WinRM Configurations
Note: If you have already executed the ConfigureRemotingForAnsible.ps1 successfully, you can directly try the connection from an Ansible machine. Below step is to ensure that WinRM is working from same managed node.
Open a command prompt or powershell and execute winrm e winrm/config/listener.
C:\Users\Administrator>winrm e winrm/config/listener
Listener
Address = *
Transport = HTTP
Port = 5985
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint
ListeningOn = 10.0.2.15, 127.0.0.1, 192.168.99.103, ::1, fe80::5efe:10.0.2.15%3, fe80::5efe:192.168.99.103%13, fe80::785d:9659:c4d4:9b0f%16
Listener
Address = *
Transport = HTTPS
Port = 5986
Hostname = WIN-CCUQI8Q4RMH
Enabled = true
URLPrefix = wsman
CertificateThumbprint = 64E69568BD75F3068BDCBF7ED819E4EA9ED1FDA3
ListeningOn = 10.0.2.15, 127.0.0.1, 192.168.99.103, ::1, fe80::5efe:10.0.2.15%3, fe80::5efe:192.168.99.103%13, fe80::785d:9659:c4d4:9b0f%16Check WinRM Configuration
C:\Users\Administrator>winrm get winrm/config
Config
MaxEnvelopeSizekb = 500
MaxTimeoutms = 60000
MaxBatchItems = 32000
MaxProviderRequests = 4294967295
Client
NetworkDelayms = 5000
URLPrefix = wsman
AllowUnencrypted = false
Auth
Basic = true
Digest = true
Kerberos = true
Negotiate = true
Certificate = true
CredSSP = false
DefaultPorts
HTTP = 5985
HTTPS = 5986
TrustedHosts
Service
RootSDDL = O:NSG:BAD:P(A;;GA;;;BA)(A;;GR;;;IU)S:P(AU;FA;GA;;;WD)(AU;SA;GXGW;;;WD)
MaxConcurrentOperations = 4294967295
MaxConcurrentOperationsPerUser = 1500
EnumerationTimeoutms = 240000
MaxConnections = 300
MaxPacketRetrievalTimeSeconds = 120
AllowUnencrypted = true
Auth
Basic = true
Kerberos = true
Negotiate = true
Certificate = false
CredSSP = false
CbtHardeningLevel = Relaxed
DefaultPorts
HTTP = 5985
HTTPS = 5986
IPv4Filter = *
IPv6Filter = *
EnableCompatibilityHttpListener = false
EnableCompatibilityHttpsListener = false
CertificateThumbprint
AllowRemoteAccess = true
Winrs
AllowRemoteShellAccess = true
IdleTimeout = 7200000
MaxConcurrentUsers = 2147483647
MaxShellRunTime = 2147483647
MaxProcessesPerShell = 2147483647
MaxMemoryPerShellMB = 2147483647
MaxShellsPerUser = 2147483647
C:\Users\Administrator>
Verify Port Connection
You can verify connectivity using any method but since I am using this for Ansible, I will check the port connection from my Ansible machine (Any linux machine)
$ nc -vz 192.168.99.103 5985
Connection to 192.168.99.103 port 5985 [tcp/wsman] succeeded !That’s it, now you can access your Windows machine over WinRM and Ansible will be able to execute playbook and tasks on your Windows machine.
Disclaimer:
The views expressed and the content shared in all published articles on this website are solely those of the respective authors, and they do not necessarily reflect the views of the author’s employer or the techbeatly platform. We strive to ensure the accuracy and validity of the content published on our website. However, we cannot guarantee the absolute correctness or completeness of the information provided. It is the responsibility of the readers and users of this website to verify the accuracy and appropriateness of any information or opinions expressed within the articles. If you come across any content that you believe to be incorrect or invalid, please contact us immediately so that we can address the issue promptly.
Tags:
Comments
5 Responses
Leave a Reply





[…] Read How to open WinRM ports in the Windows firewall. […]
Also read how to configure Windows machine for Ansible to manage.
https://www.techbeatly.com/2020/12/configure-your-windows-host-to-manage-by-ansible.html
I was looking for the same. Thank you.
[…] simple as in the document. You need to configure and enable WinRM on your Windows machine and then open WinRM ports 5985 and 5986(HTTPS) in the Windows Firewall (and also in the network firewall if […]
[…] How to open WinRM ports in the Windows firewall […]